Look, I’m going to be straight with you about something that makes most people uncomfortable. Last month, I found a missing teenager in four hours using nothing but Instagram and TikTok. The police had been searching for three days. Her parents were beside themselves. And I’m sitting there with my laptop, tracking down digital breadcrumbs that led us straight to her.
I’ve been doing this kind of digital investigation for eight years now – started when I was helping divorce attorneys verify claims about custody and assets. What began as occasional consulting work turned into something I never expected: I can find almost anyone, anywhere, using just their social media footprint.
Here’s what bothers me about this whole topic. Everyone acts like online privacy is this mystical thing that’s either completely secure or completely blown. That’s bullshit. The truth is, most people are broadcasting their exact location dozens of times a day without realizing it, while others think they’re invisible when they’re actually leaving digital fingerprints everywhere.
Why Most People Have No Clue How Exposed They Are
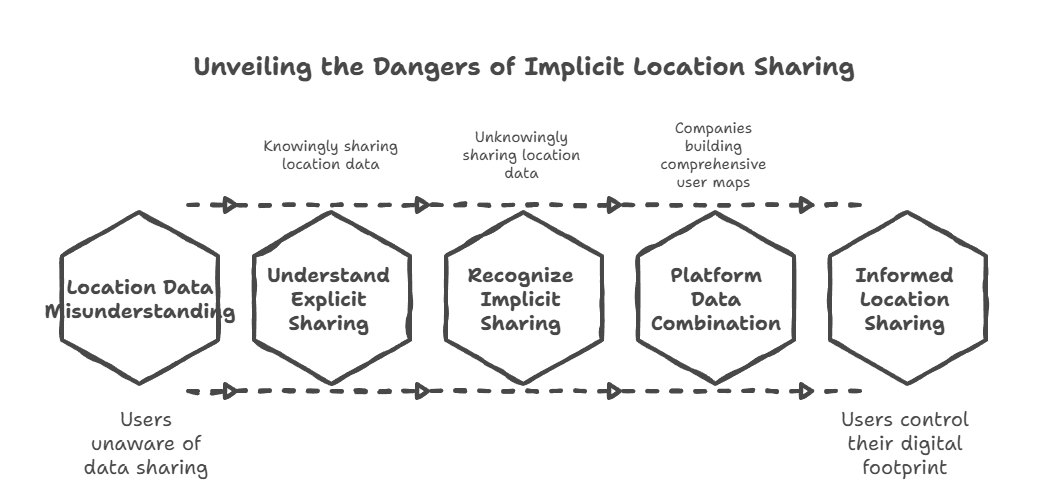
The biggest problem isn’t that social media platforms collect location data – it’s that people have zero understanding of what they’re actually sharing.
I had this client whose ex-husband was violating a restraining order but claiming he was in another state. Took me 20 minutes to prove he was lying. His Spotify playlist was location-tagged to a coffee shop three blocks from her house. His Instagram story showed a reflection in his sunglasses that clearly showed the street sign outside her gym. His LinkedIn check-in was at a networking event downtown.
This guy thought he was being smart by not posting obvious photos or checking in directly. But every app on his phone was quietly documenting his movements and sharing them in ways he never considered.
Here’s the thing that kills me – this wasn’t some sophisticated hacking. This was basic information available to anyone who knew where to look. And that’s exactly the problem.
How Location Data Really Works (The Stuff They Don’t Tell You)
People think location sharing means checking in at restaurants. That’s kindergarten stuff. The real tracking happens in the background, and it’s way more sophisticated than most people realize.
Explicit sharing is obvious – you post a photo and tag your location, or check in somewhere. But implicit sharing is where things get interesting and scary.
Every photo you take has metadata embedded in it, including GPS coordinates down to within three feet of where you took it. Post a selfie from your bedroom window? I can find your house. Share a picture of your morning coffee? I know which coffee shop you go to and what time you’re usually there.
WiFi networks have unique identifiers. When your phone connects to your home network, then later connects to the Starbucks network, then your gym’s network, apps can map your daily routine with incredible precision.
The scariest part? This data gets combined across platforms. The same company that owns Instagram also owns Facebook and WhatsApp. They’re not looking at your Instagram location in isolation – they’re building a comprehensive map of your life.
I tested this myself. Created a brand new Instagram account, posted three photos over a week with no location tags. Within two weeks, Instagram was suggesting I follow people who worked in my office building. How did it know? Location correlation between my new account and existing users who were frequently in the same places.
The Techniques I Actually Use (From Basic to Advanced)
Level 1: Basic Detective Work
Most people I find aren’t hiding – they just don’t realize how much they’re sharing.
Name and keyword searches are your starting point, but you’ve got to be smart about it. Don’t just search “John Smith” – that’s useless. Search “John Smith” + “software engineer” + “Denver.” Or “John Smith” married to “Sarah” with kids named “Emma.”
I found a custody case witness by searching her unusual first name plus her dog’s name (which she posted about constantly). Took me 15 minutes.
Hashtag analysis tells you where people hang out. Someone who posts #denverbroncos, #redrockspark, and #16thstreetmall clearly lives in Denver. But it goes deeper than that. #MondayMotivation posts from the same gym every week? That’s their regular workout schedule. #TacoTuesday always from the same restaurant? That’s their weekly routine.
Level 2: Advanced Pattern Recognition
This is where it gets interesting. You’re not just looking for obvious clues – you’re building behavioral profiles.
Cross-platform correlation is my secret weapon. People use different names on different platforms, but they make similar posts. Guy calls himself “Mike_Denver23” on Instagram but “Michael_Colorado” on Twitter. Both accounts post about the same obscure hobby at similar times, follow similar accounts, use similar phrases. It’s the same person.
I track posting patterns because people are creatures of habit. Someone who posts workout selfies every Tuesday at 6 AM from the same mirror angle? I know their gym schedule. Friday night dinner posts always from restaurants within a five-mile radius of each other? I know their neighborhood.
Platform-specific advantages matter. Instagram’s location tags are more accurate than Facebook’s. Twitter’s advanced search can find tweets from specific coordinates. LinkedIn shows workplace locations even when people try to hide their home address. TikTok’s “Find Friends” feature shows mutual connections in ways other platforms don’t.
Level 3: The Stuff That Scares Me
Here’s where it gets into territory that makes me uncomfortable, but you need to know this exists.
Third-party data aggregation sites pull information from dozens of sources. Spokeo, WhitePages, Pipl – these aren’t just people search engines. They’re combining social media data with public records, purchasing history, and leaked databases to build comprehensive profiles.
I can search someone’s email address and get their home address, family members, previous addresses, phone numbers, and social media profiles in about 30 seconds. Cost me $19.95.
Reverse image searching catches people lying about locations. Someone posts a photo claiming they’re in Miami, but reverse search shows that same image was posted by someone else in Nashville two years ago. People steal photos all the time, but they don’t realize how easy it is to catch them.
Mobile tracking through apps is the nuclear option. Apps like Find My Friends, Life360, and Snapchat’s Snap Map show real-time locations if people have them enabled. Most people forget they turned these on.
I helped find a runaway teenager because she had Snapchat’s location sharing turned on. Her parents could see exactly where she was every time she opened the app. Took us straight to her.
The Legal and Ethical Minefield (This Is Critical)
Let me be crystal clear about something: just because you can find information doesn’t mean you should use it, and definitely doesn’t mean you can do anything you want with it.
The stalking line is real. I’ve had law enforcement contact me about people who hired me for “background checks” that turned out to be harassment campaigns. Now I screen every client and every request. If someone gives me red flags about why they need the information, I don’t take the job.
Here’s my personal rule: if someone has made their information publicly available through their own social media posts, that’s fair game for legitimate purposes. If I have to use leaked databases, hacked information, or deceive someone to get access to their private accounts, that’s crossing the line.
Legitimate uses include: finding missing persons, verifying information in legal cases, background checks for employment, confirming someone’s identity for business purposes, helping people reconnect with lost family members.
Illegitimate uses include: stalking, harassment, doxxing, blackmail, revenge, or anything that could cause harm to someone who hasn’t done anything wrong.
The legal landscape is constantly changing. GDPR in Europe, CCPA in California, and dozens of other privacy laws affect what information can be collected and how it can be used. I’m not a lawyer, but I work with several, and they tell me this stuff gets more complicated every year.
How to Verify What You Find (Because People Lie)
Social media is full of lies, old information, and people pretending to be someone they’re not. Always verify.
Cross-reference multiple sources. If someone’s LinkedIn says they work at Microsoft in Seattle, but their Instagram shows them at Miami Beach every day, something’s wrong. Maybe they work remotely, maybe they’re unemployed, maybe the LinkedIn is outdated. Don’t assume anything.
Check timestamps and dates. I caught someone violating parole because they posted a photo claiming to be at their halfway house, but the metadata showed the photo was taken six months earlier. They’d saved an old photo and reposted it to fake their location.
Use reverse image searches religiously. Google Images, TinEye, and Yandex can tell you if someone’s profile photo is actually a stock image or stolen from someone else’s account. I’ve found dozens of fake profiles this way.
Protecting Yourself (Because You’re Probably Screwing This Up)
After seeing how easy it is to find people, I completely changed how I use social media. Here’s what actually works to protect your privacy:
Turn off location services for everything that doesn’t absolutely need it. Your weather app needs location. Your calculator doesn’t. Go through every app on your phone and revoke location access unless there’s a specific reason it needs to know where you are.
Strip metadata from photos before posting. iPhone’s settings let you remove location data from shared photos. Android has similar options. Use them, or use apps that strip metadata automatically.
Be paranoid about check-ins and location tags. Never post where you are in real-time. If you want to share vacation photos, wait until you’re home. Broadcasting that you’re not home is asking for trouble.
Review your privacy settings monthly. Platforms change their privacy policies and default settings constantly. What was private last month might be public now. Set calendar reminders to check this stuff.
Think about reflection and background details in photos. I’ve identified locations from street signs in reflections, addresses on mail in the background, and unique architectural features visible through windows. If you’re posting photos from home, be careful what else is visible.
Use different usernames across platforms. Don’t make it easy to connect your accounts. “MikeJohnson_Denver” on every platform might as well be a roadmap to your life.
Most importantly: assume everything you post online is permanent and public. Even if you delete it, someone might have screenshot it. Even if your account is private, friends can share your content. Act accordingly.
Real Cases That Show How This Works
Case 1: The Custody Fraud
Had a father claiming he couldn’t afford child support because he’d lost his job and was living in his car. His ex-wife hired me because something felt off. Took me three hours to prove he was lying.
His Instagram showed him at expensive restaurants twice a week. His LinkedIn still listed him as employed. His Venmo transactions (which he had set to public like an idiot) showed payments for rent at a nice apartment complex. His Apple Watch fitness data was posting to social media, showing he was working out at a high-end gym.
The judge was not amused. Guy ended up owing $15,000 in back support plus penalties.
Case 2: The Missing College Student
Parents called me when their daughter missed three days of classes and wasn’t answering her phone. Police said they had to wait 48 hours. I found her in 90 minutes.
Her Instagram story showed she was at a music festival three states away – something her parents didn’t know about. But the location tag was wrong. Reverse image search showed the photos were from last year’s festival. Her Spotify was still playing music from her dorm room.
Found her passed out drunk in her dorm. She’d been too embarrassed to tell her parents she’d failed an important test and was hiding in her room. Not the worst outcome, but her parents were relieved.
Case 3: The Corporate Espionage
Company hired me because they suspected a competitor was stealing their clients through an inside source. Took me a week to identify the leak.
Employee was posting LinkedIn updates about “exciting new opportunities” right before clients jumped ship. His Twitter showed him at lunch meetings with people who worked for the competitor. His Instagram had photos from company events where confidential documents were visible in the background.
Wasn’t sophisticated espionage – just an idiot who didn’t realize he was documenting his own crimes on social media.
What’s Coming Next (And Why It’s Terrifying)
The technology is getting scarier every year. AI-powered facial recognition can identify people from a single photo across multiple platforms. Upload someone’s picture to certain tools, and they’ll find every social media account associated with that face.
Real-time location tracking through IoT devices is expanding beyond phones. Smart cars, fitness trackers, even smart home devices can be used to track movements. I worked a case where we tracked someone through their Tesla’s location data – the car was automatically posting to social media when it charged at different stations.
Behavioral prediction algorithms are getting sophisticated enough to predict where someone will be based on their patterns. If you go to Starbucks every Tuesday at 8 AM for six months, AI can predict you’ll be there next Tuesday even if you don’t post about it.
The privacy tools aren’t keeping up with the tracking technology. Every year it gets easier to find people and harder to stay hidden.
The Bottom Line
Here’s what I want you to understand: this isn’t about being paranoid or avoiding social media completely. It’s about being intentional with what you share and realistic about privacy in 2025.
I can find almost anyone in a few hours if they use social media normally. That’s not a threat – that’s just reality. But I can also help people protect themselves if they understand how the system works.
The people who stay safe aren’t the ones who avoid technology – they’re the ones who understand it well enough to use it on their terms instead of letting it use them.
Start by auditing your own digital footprint. Search for yourself the way I’d search for you. See what information is publicly available. Then decide what you’re comfortable with and lock down everything else.